Cybersecurity Essentials
Protect systems, networks, and data with our best cyber security course designed for real-world defense strategies. This cyber security certification course equips you with essential skills to detect threats, prevent cyberattacks, and secure digital assets all through expert-led training and hands-on simulations.
Level : Advance
Duration :240 hrs
Rating : 4.8/5
Language : Linux
Activate this Course for :
₹ 17999
17999
Activate this Course for :
₹ 18999
18999
Enter Details
Cybersecurity Essentials Course Overview
A deep understanding of cyber threats, ethical hacking, and risk management
Hands-on labs in penetration testing, malware analysis, and firewall configuration
Techniques to secure cloud, network, and application-level environments
Real-time attack simulations and incident response planning
Guidance to earn leading cybersecurity certifications recognized across industries
Cybersecurity Essentials Course Includes
Certification After completing the courses
We Provides 24/7 Dedicated Forum Support
Accessing to AI tools to enhance coding skills
Enjoy Lifetime access to course materials
Assessments to track your progress
Cybersecurity Essentials Course Contents
-
1.1.What is Cybersecurity & Ethical Hacking?
-
1.2.Hacking Terminologies & Phases
-
1.3.Installing VirtualBox & Kali Linux
-
1.4.Setting up vulnerable OS (Metasploitable OWASP-BWA)
-
1.1.What is Cybersecurity & Ethical Hacking?
-
1.2.Hacking Terminologies & Phases
-
1.3.Installing VirtualBox & Kali Linux
-
1.4.Setting up vulnerable OS (Metasploitable OWASP-BWA)
-
2.1.APT & DPKG commands
-
2.2.Repository setup & updates
-
2.3.Kali walkthrough
-
2.4.OSINT Framework
-
2.5.Google Hacking web analysis techniques
-
2.1.APT & DPKG commands
-
2.2.Repository setup & updates
-
2.3.Kali walkthrough
-
2.4.OSINT Framework
-
2.5.Google Hacking web analysis techniques
-
3.1.OSI & TCP/IP Architecture
-
3.2.Network Topologies
-
3.3.Host & Port Scanning (Nmap)
-
3.4.HTML scan reports custom port scan scripting
-
3.5.DNS analysis
-
3.1.OSI & TCP/IP Architecture
-
3.2.Network Topologies
-
3.3.Host & Port Scanning (Nmap)
-
3.4.HTML scan reports custom port scan scripting
-
3.5.DNS analysis
-
4.1.Vulnerability scanning with NSE & Nmap
-
4.2.Searchsploit for known exploits
-
4.3.NGROK Setup: Hosting tunneling concepts
-
4.4.Dynamic vs Static IPs
-
4.1.Vulnerability scanning with NSE & Nmap
-
4.2.Searchsploit for known exploits
-
4.3.NGROK Setup: Hosting tunneling concepts
-
4.4.Dynamic vs Static IPs
-
5.1.Sniffing & Spoofing explained
-
5.2.ARP Poisoning
-
5.3.Session Hijacking
-
5.4.Tabnabbing attacks
-
5.5.Wireshark basics
-
5.1.Sniffing & Spoofing explained
-
5.2.ARP Poisoning
-
5.3.Session Hijacking
-
5.4.Tabnabbing attacks
-
5.5.Wireshark basics
-
6.1.Wordlist creation using Crunch
-
6.2.FTP Zip password attacks
-
6.3.Hash cracking (MD5 SHA1)
-
6.4.Rainbow Tables & Hashcat
-
6.1.Wordlist creation using Crunch
-
6.2.FTP Zip password attacks
-
6.3.Hash cracking (MD5 SHA1)
-
6.4.Rainbow Tables & Hashcat
-
7.1.Introduction to MSF & Payloads (MSFVenom)
-
7.2.Reverse connections
-
7.3.Port forwarding techniques
-
7.4.Post-exploitation modules
-
7.5.Real-time malware injection (safe environment)
-
7.6.Anti-forensics & cleanup techniques
-
7.1.Introduction to MSF & Payloads (MSFVenom)
-
7.2.Reverse connections
-
7.3.Port forwarding techniques
-
7.4.Post-exploitation modules
-
7.5.Real-time malware injection (safe environment)
-
7.6.Anti-forensics & cleanup techniques
-
8.1.Social Engineering Toolkit
-
8.2.Phishing: Local & over the Internet
-
8.3.IP Obfuscation
-
8.4.Android payloads & reverse shells
-
8.5.Real-world phishing simulation (education-focused only)
-
8.1.Social Engineering Toolkit
-
8.2.Phishing: Local & over the Internet
-
8.3.IP Obfuscation
-
8.4.Android payloads & reverse shells
-
8.5.Real-world phishing simulation (education-focused only)
-
9.1.Dirb & Dirbuster for hidden paths
-
9.2.Burp Suite usage
-
9.3.XSS: Reflected & Stored
-
9.4.SQL Injection basics
-
9.1.Dirb & Dirbuster for hidden paths
-
9.2.Burp Suite usage
-
9.3.XSS: Reflected & Stored
-
9.4.SQL Injection basics
-
10.1.Keyloggers (manual & automated)
-
10.2.DOS & DDOS concepts
-
10.3.IDS/IPS & Honeypots
-
10.4.Security layers & protection mechanisms
-
10.5.Data privacy Dark Web Surface Web
-
10.1.Keyloggers (manual & automated)
-
10.2.DOS & DDOS concepts
-
10.3.IDS/IPS & Honeypots
-
10.4.Security layers & protection mechanisms
-
10.5.Data privacy Dark Web Surface Web
-
11.1.Cryptography types & hashing functions
-
11.2.Blockchain basics & architecture
-
11.3.Use cases: Smart contracts & secure ledgers
-
11.4.Bitcoin Ethereum & Hyperledger intro
-
11.1.Cryptography types & hashing functions
-
11.2.Blockchain basics & architecture
-
11.3.Use cases: Smart contracts & secure ledgers
-
11.4.Bitcoin Ethereum & Hyperledger intro
-
12.1.Mini project: Penetration testing report
-
12.2.Simulated Bug Bounty Lab walkthrough
-
12.3.Covering tracks using anti-forensics
-
12.4.Documentation reporting resume building
-
12.5.Viva + Assessment
-
12.1.Mini project: Penetration testing report
-
12.2.Simulated Bug Bounty Lab walkthrough
-
12.3.Covering tracks using anti-forensics
-
12.4.Documentation reporting resume building
-
12.5.Viva + Assessment
Benefits
Our Dashboard offers 1500+ coding problems to sharpen skills and prepare for company-specific interviews. Track progress, build your profile, and boost job-readiness for successful technical interviews
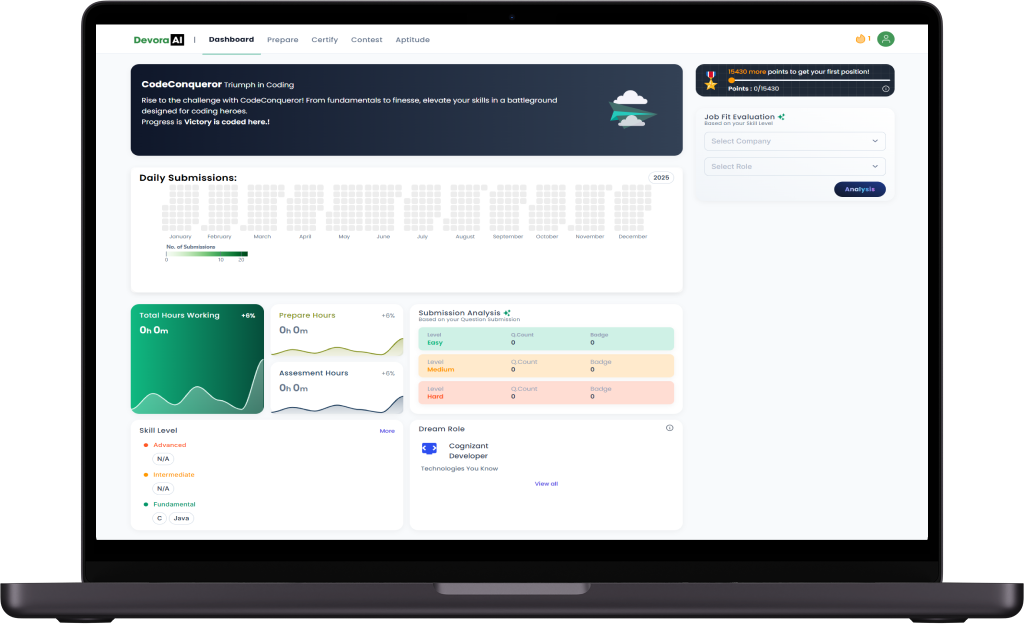
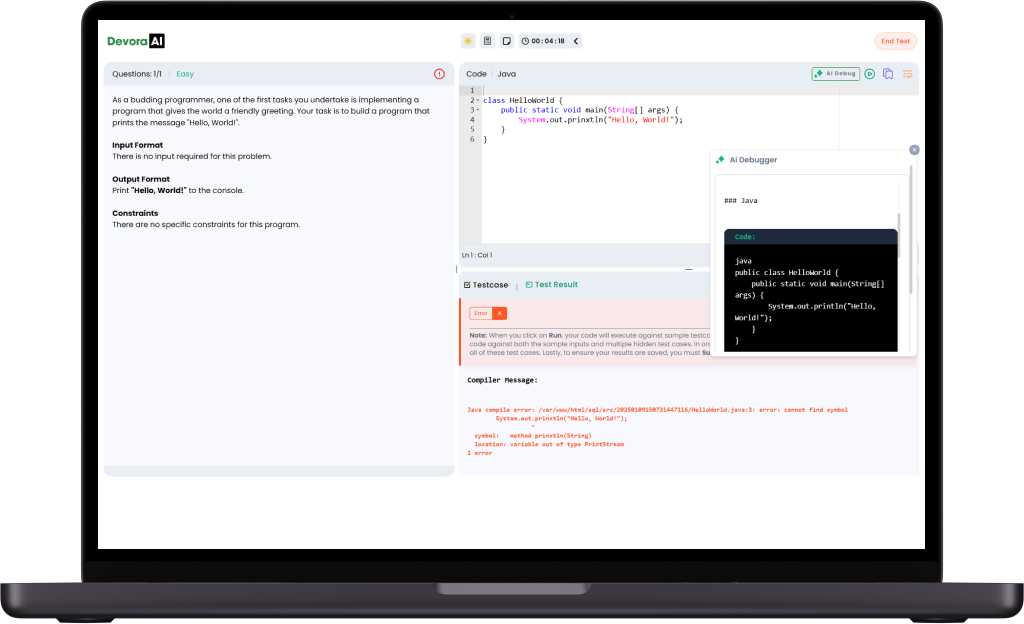
Our product provides real-time debugging assistance, allowing learners to efficiently identify and fix errors, enhancing their programming skills and understanding
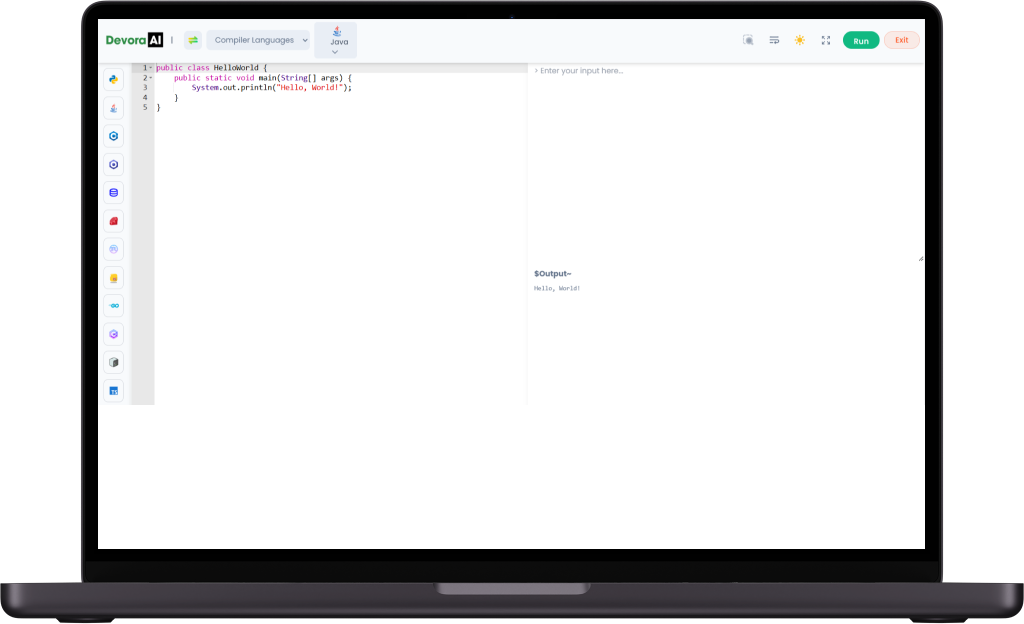
Our integrated IDE compiler offers a unified platform for writing, executing, and debugging code efficiently. With real-time execution and instant feedback, users can test and optimize their code seamlessly.
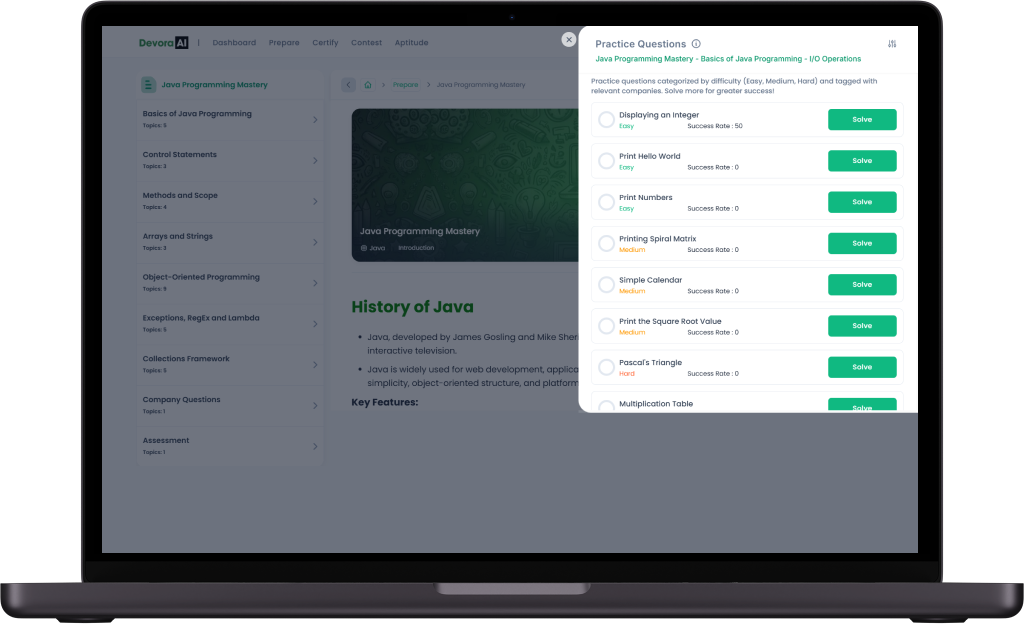
we organize coding contests within the platform, offering users the opportunity to compete against peers, test their problem-solving abilities, and enhance their skills through time-bound challenges and real-world scenarios
We maintain a personalized profile for each user, tracking their learning progress, performance in coding problems, and achievements,It also includes a record of completed contests, certifications earned, and coding skills developed etc
This is one For You
Hands on training
Looking to enhance your Coding skills
Innovation Ideas
lets you create innovative solutions, explore technologies
Newbie Programmer
Budding Programmer , Wants to learn some tricks and tips
Upskilling your skills
A professional wanting to Update their skills
Gain a Competitive Edge With Our Professional Certificates

Master the latest programming languages and enhance your skill set with a recognized certificate.
unlock new career opportunities with a programming certificate


